Ransomware from Darkside Amplifies Threat Actors
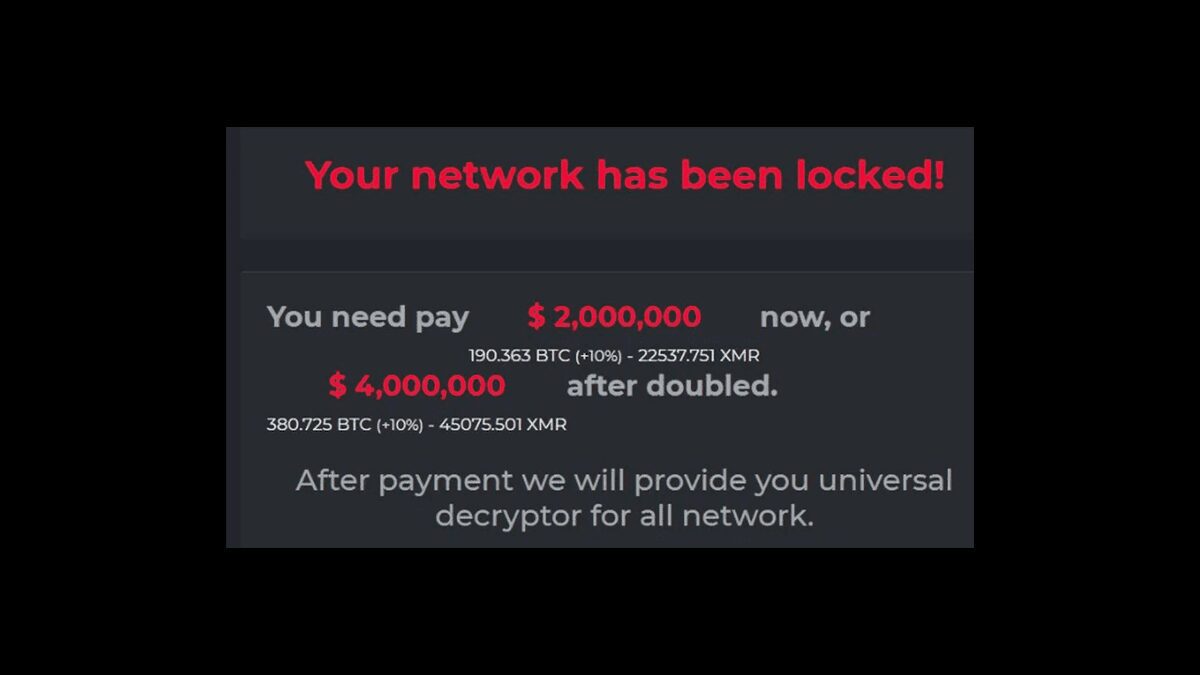
Cybercriminals no longer need to invent new ways to penetrate and compromise a target organization. Darkside, a criminal organization based in Russia, is apparently in the business of offering ransomware as a service to other criminal actors on the Internet. This time, Colonial Pipeline, one of the largest energy transportation operators in the Eastern United States, revealed last weekend their IT systems have been compromised using software distributed by Darkside. The FBI confirmed that Darkside software was used in the attack. The attack led to Colonial shutting down the largest gasoline pipeline in the Eastern United States in an abundance of caution.
Ransomware as a Service
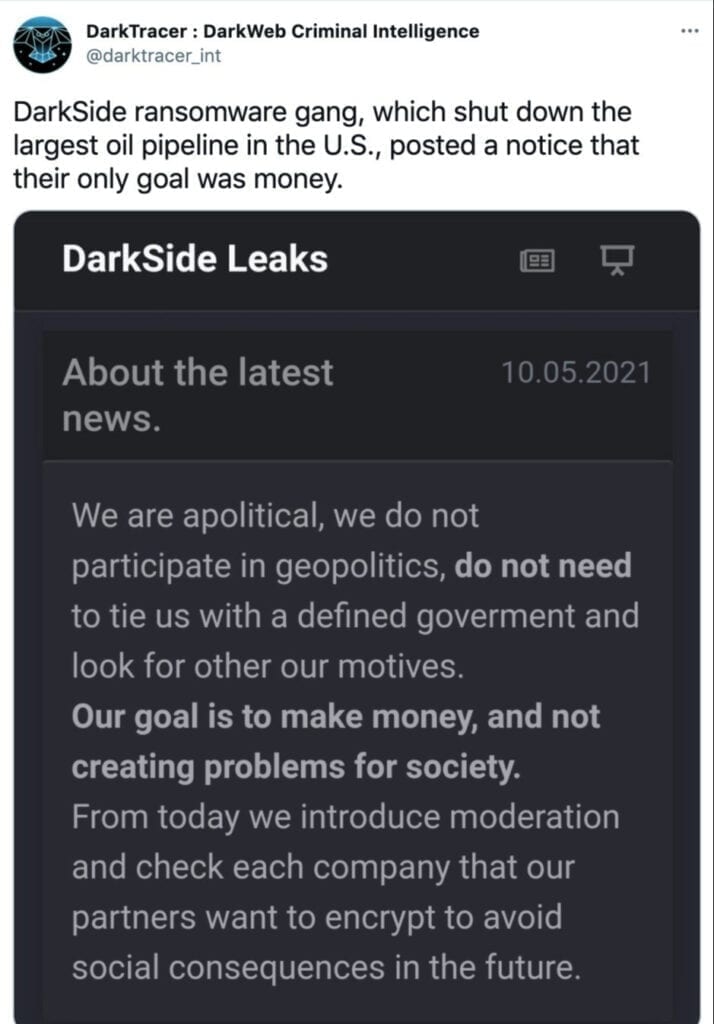
Darkside purports to operate as an “ethical” hacker, raking in extortion profits from poorly operated IT networks in the West. It then acts like a proverbial Robin Hood by sharing profits with charities. Now, other extortionists who wish to commit drive-by criminal acts like Darkside can apparently use Darkside’s technology and services. That is also apparently what happened in the Colonial case. One of Darkside’s claims is that a client of theirs went too far in case of Colonial.
Threats are Growing
This is not the first time that criminal networks have been available to the highest bidder. In 2013 the FBI and Microsoft took down a Denial of Service (DoS) botnet called Citadel. Citadel would then take down a selected website for a fee. Now, with Darkside’s encryption system, and easy-to-use command-and-control (C2) systems, any determined group can put together an attack.
And now may of these threats surround the software supply chain. See additional coverage on the SolarWinds and Codecov hacks.
Now that criminal networks are starting to look like multi-level-marketing organizations, it is possible for the threat to grow exponentially. Insurance companies and the cryptocurrencies which support the paying of a demand in a ransomware attack must be examined closely. These businesses exacerbate the problem by allowing bitcoin, “cyberinsurance,” and other financial products that support the ransomware industry.
Guard your Perimeter
The ongoing cyber war between legitimate businesses and a growing industry of threat actors makes hardening the Salesforce devops process from the inside out more important than ever. Do not forget to add perimeter security and social engineering awareness to your Salesforce devops toolkit, starting today.
We must remember that many of the “drive by attacks,” or random attacks on any commercial entity, come from well-known phishing vectors involving a user and an endpoint. Technology can help keep out the random threats, so it is time to add endpoint security, hardware SD-WAN/VPN, and MFA to the Salesforce devops toolkit.
In targeted attacks, threat actors now use social media and big data techniques to target specific employees. In these kinds of social engineering attacks, employees need training and awareness as a starting place for a defensive strategy.